Configuring ITM On-Prem (ObserveIT) Identification Services
When multiple users have access to a generic account (such as the default Administrator account), it can be difficult, even impossible to identify the actual person who is using the account. By enabling and configuring ObserveIT's Identification Services, the system can be configured to require users that log on to the monitored endpoints to identify themselves with a secondary ITM On-Prem (ObserveIT) log on prompt, before they can access a Windows server desktop or a published application. On Linux/Unix Agents, generic users with shared user accounts (such as "root" or "sysadmin") will be prompted to enter their secondary credentials before they can open an interactive user session on an ObserveIT-monitored Linux/Unix computer. These users are also known as "Forced-Identification" users. The exact names of Forced-Identification users is decided by the client, based on the client configuration and particular needs. The names should include user accounts that are widely known, to enable more than one person to use them for logging on to the monitored systems.
The Identification Services feature is supported on Windows and Unix/Linux Agents.
ObserveIT's Identification Services can integrate with Active Directory. After completing the Windows/Unix logon process, users receive a secondary ITM On-Prem (ObserveIT) logon prompt, in which they must enter their own personal user name and password before continuing (see Forced-Identification User Login). These user credentials are then checked against an Active Directory source. When no central Active Directory is available against which ITM On-Prem (ObserveIT) Identification services can authenticate, you can define local ITM On-Prem (ObserveIT) targets for user authentication. In this case, after users enter their personal user name and password during ITM On-Prem (ObserveIT) Identification Services log on, their credentials can be checked against a predefined list of ITM On-Prem (ObserveIT) local users.
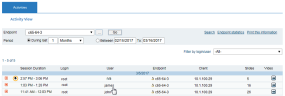
When Identification Services are configured and a Forced-Identification user has successfully logged in, in the ITM On-Prem Web Console (Endpoint Diary, User Diary, Search, or Reports page) you can view the name of the user who logged in with the shared user account. For example:
When Identification Services are not configured, the only information available is the login name.
To configure the ITM On-Prem (ObserveIT) Identification Services
-
Create Forced-Identification users. Creating these users does not affect any actual user accounts; it simply instructs ITM On-Prem (ObserveIT) to require identification when any of these users log on to any ObserveIT-monitored endpoint. For details, see Configuring Forced-Identification Users.
-
Configure the authentication targets for these users. Identification is performed against one or more LDAP targets (or domains) by adding Active Directory identification targets. When no central Active Directory is available against which ITM On-Prem (ObserveIT) Identification services can authenticate, you will need to use local ITM On-Prem (ObserveIT) targets for user authentication. For details, see Configuring Active Directory Identification Targets and Configuring Local ITM On-Prem (ObserveIT) Identification Users.
-
Configure which Active Directory groups can authenticate to the secondary ITM On-Prem (ObserveIT) logon. If the LDAP target is an "Automatic"-type, you can prevent users who are not members of a predefined Active directory group from gaining access and logging on to the monitored endpoints. For details, see Configuring Active Directory Console Groups.
-
Later, if required, you can configure either a Manual Server Policy or Server Policies to configure which endpoint will be affected by the new Identification Policy. For details, see Identification Policy.
To apply secondary authentication for ITM On-Prem (ObserveIT) users on Unix/Linux Agents, you must first enable secondary authentication for Unix/Linux policies in the ITM On-Prem Web Console. For details, see Enabling Secondary Identification for Linux/Unix Policies.