Configuring Active Directory Groups for Forced-Identification Users
By integrating ITM On-Prem (ObserveIT) with Active Directory, you can configure Identification Services so that no user can pass the ITM On-Prem (ObserveIT) Identification screen unless they are members of a specific Active Directory group. In this way, you can prevent users who are not members of a predefined Active directory group from gaining access to the Windows desktop and logging on to the monitored endpoints.
Using Active Directory groups is only possible if the LDAP target is an "Automatic"-type LDAP Target. For further details, see Configuring Active Directory Identification Targets.
By default, all Active Directory groups can authenticate. You can exclude specific groups from being able to authenticate, or allow only specific groups to authenticate. In the Active Directory Groups section of the Configuration > Security & Privacy > Identification page, you can include and exclude Active Directory groups from the specified Active Directory domain.
To include or exclude Active Directory groups from a domain
-
Navigate to the Configuration > Security & Privacy > Identification page and add Forced-Identification user(s). For further details, see Configuring Forced-Identification Users.
-
In the Active Directory Identification Targets section, make sure that there is an "Auto"-type Active Directory Domain. If no "Auto"-type domain exists, you will not be able to use Active Directory groups.
- In Active Directory Users and Computers, create the required group(s) and add members to them.
In the following example, two groups are defined in the domain OIT-DEMO.LOCAL:
- no-oit-logon: All users can authenticate in the ITM On-Prem (ObserveIT) Identification screen, except users that are members of this group (in this case, user1 and user2).
- yes-oit-logon: Only users that are members of this group can authenticate in the ITM On-Prem (ObserveIT) Identification screen.
-
If you want to configure the ITM On-Prem (ObserveIT) Identification Service to allow access to all Active Directory groups except those in the Exclude list:
-
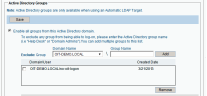
Select Enable all groups from this Active Directory domain.
-
In Exclude: Group, enter the domain name of the Active Directory group that you want to exclude from the Identification Service, or select it from the list of all the domains in the Active Directory forest in which the ITM On-Prem (ObserveIT) Application Server is a member.
In order to use domain local groups, you must enable the "Allow LDAP local groups" option in the System Settings page of the Web Console.
- Enter the group name that you want to exclude (in this case, no-oit-logon), and click Add.
-
Click Save.
If you forget to click Save, the Active Directory group integration will not work.
As a result, when a user logs on to a monitored server by using the Administrator account, if they enter "user1" or "user2" in the ITM On-Prem (ObserveIT) Identification screen, they will not be able to gain access to the desktop, because these users are members of the no-oit-logon group. However, if "user3" attempts to authenticate, they will be granted access to the desktop.
-
- If you want to configure the ITM On-Prem (ObserveIT) Identification Service to deny access to all Active Directory groups except those in the Enable list:
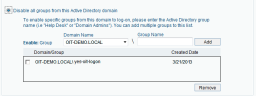
Select Disable all groups from this Active Directory domain.
In Enable: Group, enter the domain name of the Active Directory group that you want to enable access to the Identification Service, or select it from the list of all the domains in the Active Directory forest in which the ITM On-Prem (ObserveIT) Application Server is a member.
Enter the group name that you want to enable (in this example, yes-oit-logon). Click Add.
The group name will be verified against the Active Directory domain, therefore you must make sure that the group already exists in the domain.
- Click Save.
As a result, when "user3" attempts to authenticate, they will be granted access to the desktop, but "user1" and "user2" will not be able to gain access to the desktop, because they are not members of the yes-oit-logon group.