Exposing Personal Information for Specific Users
When "Anonymization" is enabled in the ITM On-Prem Web Console (see Enabling/Disabling Anonymization), recorded users' personal information is hidden in the ITM On-Prem Web Console unless specifically requested and approved to be exposed.
Any Web Console user can make a request to expose users' personal information, but only a Privacy Officer can approve the request.
The Privacy Officer can exclude specifically requested users from having their personal identifiable information anonymized by:
-
Defining users or AD groups whose personal details should not be anonymized. See Excluding Users From Being Anonymized.
-
Allowing specific Web Console users to view all user personal data in the clear. See Permitting Users to Bypass Anonymization.
This topic describes how a Web Console user can expose the personal details of risky users who have been anonymized. The Privacy Officer can approve or reject a Web Console user's request to expose a user's personal details.
You can choose to expose only the user's personal details (photo, full name, department, role, and login account) or also the names of any computers and accounts that were accessed by the user during the session.
After a user is "de-anonymized":
-
The user's personal details will be displayed in the User Risk Dashboard.
-
In the Management Console, all session data for the user representing recorded user activity and alerts is viewable in the Latest Sessions, Endpoint and User Diaries, and Alerts pages.
To expose the personal details of a risky user that was anonymized
- Navigate to the User Risk Dashboard by clicking Insider Threat Intelligence in the ITM On-Prem (ObserveIT) Management Console.
You will see that the risky users have their personal photo, full name, department, role, and login account details anonymized.
For example:
-
Hover over the photo icon of the user you want to expose. An Expose button will appear.
-
Click the Expose button.
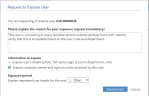
A Request to Expose User popup opens displaying the Code ID of the user whose details you want to expose.
-
Enter an explanation for the exposure request. Note that this information is mandatory.
-
Specify the information that you want to expose:
-
Expose user's details (photo, full name, department, role, login account): selected by default.
-
Expose computer names and login accounts accessed by this user: select this check box if you want to also expose all computers (servers and clients) that were accessed and all login accounts (primary and secondary) that were used.
-
-
If required, change the default period of time configured in the Anonymization tab for the user's personal details to be exposed. Specify the required number of days or weeks.
-
Click the Expose User button.
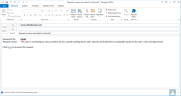
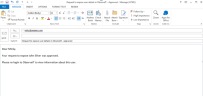
If the user who requested the exposure defined a recipient (Privacy Officer) to be notified by email regarding the new exposure request, an email notification will be sent. Clicking the here link in the email opens the User Exposure Requests page from where the request can be approved.
Following is an example:
If no recipient email addresses were configured by the user, a warning will be displayed in the Request to Expose User dialog box.
-
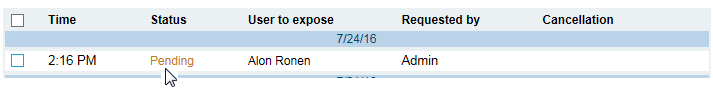
After clicking Expose User, navigate to the User Exposure Requests page (Configuration > Security & Privacy > User Exposure Requests).
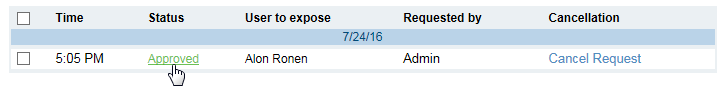
In the Requests list, you will see the exposure request displayed with a Pending status, as shown in the following example:
-
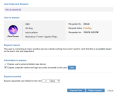
Click the Pending status link or the name of the User to expose to open the User Exposure Request details. Here, you can view and/or change the configured details for the exposure request (see Viewing and Configuring Exposure Request Details).
-
To approve the exposure request, click the Expose User button. (To cancel the exposure request, click Reject request.)
The User Exposure Request details will close and the request will appear as Approved in the Requests list.
An email notification will be sent to the requester following approval of the exposure request. For example:
You will only be able to see the changes at the next login.
The selected risky user is now de-anonymized!
In the User Risk Dashboard, you can see that the risky user's personal details are now displayed.
For example: