Windows Key Logger
When enabled in the Server Policies settings of the ITM On-Prem Web Console (see Enabling Keylogging), the ObserveIT Windows Agent key logger captures keystrokes on the recorded machine, and sends them to the Application Server, generating keyword-searchable logs.
The visual replay of user sessions is provided by the ObserveIT Session Player. For details, see Session Player.
The ObserveIT key logger for Windows-based operating systems captures keystrokes and other entered values, such as:
-
Special keys, which are Backspace, Insert, Enter, PrtScr, Clear, Return, Delete, End, Esc, and F1 to F12.
-
Combination keys, which are Alt, Ctrl, Shift and Win with another key.
-
Changed numeric values using the keyboard.
-
Changed field values that are selected from drop-down lists after pressing <Enter>.
-
Final text values after correction by using the <BACKSPACE> or <DELETE> keys.
-
Editing: When typing within a control, both the old and new versions of the text are captured.
-
Partial typing: Even if only one character within a block of text is changed, added, or deleted, the entire text, including the new character, is captured.
-
When the Auto-Complete option is used, when clicking in the field, the entire text is captured by the key logger.
-
Commands that are entered in a Windows CMD, Powershell, or Putty client window, using shortcuts, such as tab and up/down arrows. The user's commands as well as output are captured.
Searching key logger data is case-insensitive. You can search for and define alerts on data and screenshots in which the typed text was a single special character (for example, "%") or a word that contains a special character; for example, "*revenues". Note that in the case of words with special characters, you must specify the entire word when searching. Special characters include: * % ? & ! ^ +
Windows Keylogging Example
The following example provides a scenario of how keylogging works in ObserveIT on a Windows operating system.
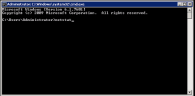
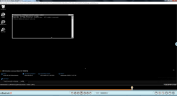
In this example, the user opens a CMD window and types the not allowedlisted command netstat (a common command line networking utility that provides information and statistics about protocols in use and current TCP/IP network connections).
The following procedures describe how to:
-
Configure an alert rule that will detect the text that the user typed, and generate an alert.
-
Search for the user activity in the Web Console, and replay the user session.
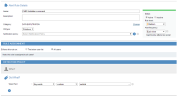
To configure an alert rule that will detect the user action and generate an alert
- In the Create Alert Rule page, configure an alert rule for the Typed Text condition, as shown in the following example:
For details on configuring the Typed Text condition, see Used Keyboard (Keylogging) Did What.
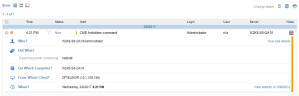
- The text is captured by the ObserveIT keylogger, and an alert will be generated and displayed in the Alerts page, as shown in the following example:
- To replay the slides of the session in which the alert occurred, click the Video
 icon to launch the ObserveIT Session Player.
icon to launch the ObserveIT Session Player.
To search for the user activity in the Web Console and replay the user session
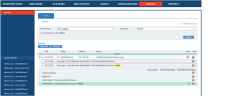
- In the Search tab of the Web Console, enter the keyword netstat in the Key Logging search option, and click Search.
The list of relevant sessions that contain the keyword netstat is displayed, as shown in the following example:
- To replay the session in which the user entered the not allowed command, click the Video
 icon of the session or the expanded session to launch the ObserveIT Session Player, as shown in the following example:
icon of the session or the expanded session to launch the ObserveIT Session Player, as shown in the following example: