Mac Keylogger
ITM On-Prem also enables you to generate alerts based on keylogger data which is captured on Mac-based desktops, laptops, or servers, as keyword-searchable logs.
To use the ITM On-Prem keylogger on monitored Mac-based machines, the key logging feature must first be enabled in the Server Policies settings of the ITM On-Prem Web Console. For details, see Enabling Key Logging.
When using the ITM On-Prem keylogger on a Mac-based operating system, note the following:
For the Terminal (Mac) application, you can define alerts and search for keywords in the command line. The command line text is captured without the prompt.
Manually typed and auto-completed (by using Tab, CTRL-T, UP/DOWN arrows) commands are captured as keylogger data; output written to the screen is not captured.
Special keys include Backspace, Insert, Enter, PrtScr, Clear, Return, Delete, End, Esc, and F1 to F12.
Key combinations are Cmd, Control, Option, and Shift with other keys.
Searching keylogger data is case-insensitive. You can search for and define alerts on data and screenshots in which the typed text was a single special character (for example, "%") or a word that contains a special character; for example, "*revenues". Note that in the case of words with special characters, you must specify the entire word when searching. Special characters include: * % ? & ! ^ + – = # @ $ ~ . , ; | < > ( ) / \ [ ] ( ) `
Mac Key Logging Example
The following example shows how captured key logging data can be used to generate an alert on a Mac operating system.
In this example, a user opens a Mac Terminal and types the command sudo-i. This is a risky command that should be avoided as it could enable the user to perform activities with 'superuser' permissions.
When the user types the command, the text is captured by the ITM On-Prem keylogger.
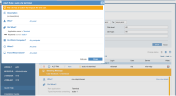
An alert rule can be configured for this action to generate an alert and display a Blocking Message to the end user, as shown in the following screenshot:
For details on how to configure the keywords that will generate the alert, see Used Keyboard (Keylogging) Did What
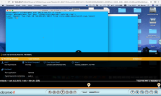
To replay the slides of the session from the point at which the alert occurred, click the Video  icon (shown above). The ITM On-Prem Session Player will be launched, displaying the details of the alert as the replay progresses:
icon (shown above). The ITM On-Prem Session Player will be launched, displaying the details of the alert as the replay progresses:
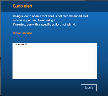
After the alert is triggered, the end user will receive a blocking message similar to the following:
Depending on the Blocking Message configuration in the alert rule, the user can be required to acknowledge the message, and provide feedback explaining their actions (in the text box provided). They might also have an option to view the company policy (as in the above example, by clicking the Superuser use hyperlink). To close the message, the user must click Submit.