Investigating Risky User Alerts
From the Risky Users area of the User Risk Dashboard, you can examine the actions of risky users, the applications they accessed, and the alerts that were triggered against them. The dashboard links directly to the Web Management Console from where you can further inspect and examine risky users and their actions. To learn more about threats and how to investigate them, see Monitoring Alerts.
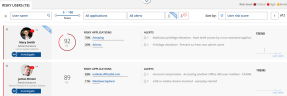
Following is an example of a Risky Users area in the User Risk Dashboard.
Clicking the  icon, you can hide the User Behavior Change area, enabling you to display more risky users on a page.
icon, you can hide the User Behavior Change area, enabling you to display more risky users on a page.
You can investigate triggered alerts according to a selected risky user, or by the individual alert.
To investigate all the alerts attributed to a risky user
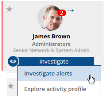
- In the Risky Users area of the User Risk Dashboard, click Investigate beneath the user you want to investigate, and select Investigate alerts.
For example:
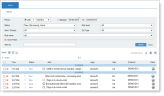
A new browser tab opens showing the Alerts tab in the Management Console, and the alerts associated with the selected user.
The alerts display is filtered to show alerts with New, Reviewing, or Issue status. Alerts with the Non-Issue status are not displayed. See also Changing the Status of Alerts.
For example:
- From the Alerts page of the Web Management Console, you can view and manage alerts (see Managing Alerts). Any changes that you make to an alert might affect the user score. For example, if you delete an alert, or change the alert status from Issue to Non-Issue, the alert score will be reduced, and this will affect the overall user risk score. For details, see Calculating User Risk Score.
To investigate an individual alert attributed to a risky user
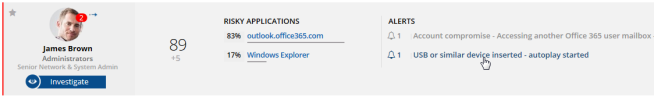
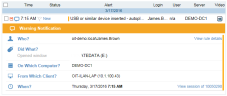
- In the Alerts list alongside the risky user you are investigating, click the specific alert you want to investigate further.
For example, if you click the alert USB or similar device inserted - autoplay started as shown below:
A new browser tab opens the Alerts page in the Management Console, displaying the alert. By clicking the alert, the exact alert details are displayed, showing who, did what, on which computer, from which client, and when the action(s) occurred.