Configuring a Unix Linux Agent to Use SSL
This procedure describes how to install a trusted internal CA certificate on a Unix/Linux server.
For information about Configuring a Self-signed certificate, see Configuring a Self-Signed Certificate.
Obtain and Import a Trusted Internal CA Certificate
If you do not already have a trusted internal CA certificate, perform the following procedure to obtain and import the certificate.
To obtain and import certificates
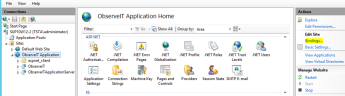
- Go to Start > run and enter inetmgr.
-
Go to ObserveIT Application, and select Bindings.
-
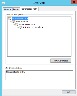
In the Site Bindings dialog box, select the https protocol and click Edit.
-
In the Edit Site Bindings dialog box, click View.
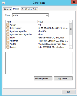
- In the Certificate dialog box, select the Certification Path tab, select the root CA certificate, and click View Certificate.
- Select the certificate's Details tab and click Copy to File.
-
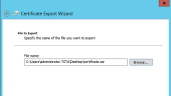
In the Certificate Export Wizard that opens, click Next.
- Select the Base-64 encoded X.509 (.CER) format option, and click Next.
- Click Browse and specify the name of the file to which you want to export the certificate.
-
Click Next and then click Finish to close the Certificate Export Wizard.
-
In the message box stating that the export was successful, click OK.
Copy the Certificates to a Linux Server
Prerequisite: See Locating the Certificates for information about verifying and locating a certificate and how to locate the /certs directory.
-
You must transfer the exported certificates to the /certs directory of the appliance, using SCP/FTP or any other protocol.
- If you are transferring the files using WinSCP, the file permissions might have changed. To verify the file permissions, run the command: ls -la
The output should look like: -rw-r--r--.
If the output looks different, change the file permissions so that "user", "group", and "other" will have read permissions. Run the following command to make the changes: chmod w+r or chmod o+r.
To enable OpenSSL to identify the certificates, link them as follows
- Extract the certificate's hash, and use it as a symbolic link to the certificate:
ln -s certificate.pem 'openssl x509 -in certificate.pem -noout -hash'.0
Or
ln -s certificate.cer `openssl x509 -in certificate.cer -noout -hash`.0
- Verify the certificate installation by running the command:
openssl verify certificate.pem
openssl verify 3ee7e181.0
Related Topics:
Configuring an ObserveIT Windows Agent to Use SSL/TLS
Configuring a Mac Agent to use SSL
** Go to Custom Installation Steps.