Mac Agent Files
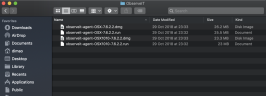
The ObserveIT Mac Agent Installation folder contains the following file:
observeit-agent-OSX-<version>.dmg
observeit-agent-OSX-<version>.dmg file contains:
observeit-agent-OSX-<version>.pkg
This is the package file for installations (remote and local).
preinstall script
This script contains the parameters for installing the Mac Agent using the observeit-agent-OSX-<version>.pkg.
Modify and use this script with:
The following is an example of the preinstall script.
preinstall script parameters
-
Server: ObserveIT Application Server hostname or IP address.
If the Agent is connected to the ObserveIT Application Server over SSL, first deploy the SSL certificate, and then in the registration address enter the Fully Qualified Domain Name (FQDN) in the format: https://FQDN:PORT/observeitapplicationserver (the default port for SSL is 443). (See Configuring a Mac Agent to use SSL.)
-
Password: Application server password.
-
Policy: Policy group ID. If not specified, the default MAC policy is used.
-
Accessibility: This option lets you decide whether you want the user to be prompted.
-
Allow Pop-up: This option lets you decide whether you want a pop-up prompt to display asking the user to allow screen recording access.
(To enable screen recording without pop-ups, see Enabling Automatic Security and Privacy Update for Mac .)
-
Process name: This option lets you assign another name to the process controller for obfuscation.
Modifying the preinstall script
-
Open the
preinstallscript. -
Modify the server parameter, by entering ObserveIT Application Server host name or IP address. For example, 10.1.100.20.
Change
echo 'SERVER=0.0.0.0' >/tmp/oit_remote_install.cfgto
-
for http:
echo 'SERVER=10.1.100.20' >/tmp/oit_remote_install.cfg -
for https (default port(443)):
echo 'SERVER=https://appserverfqdn/observeitapplicationserver' >/tmp/oit_remote_install.cfg -
for https (for any other port):
echo 'SERVER=https://appserverfqdn:PORT/observeitapplicationserver' >/tmp/oit_remote_install.cfg
-
-
Modify the ALLOWPOPUP parameter, by selecting one of the following options:
This option is available from macOS Catalina.
If you want to enable recording without the pop-ups, leave this parameter as a comment:
#echo 'ALLOWPOPUP=' >/tmp/oit_remote_install.cfg.
Enable silent recording in Enabling Automatic Security and Privacy Update for Mac .-
Change
echo 'ALLOWPOPUP=' >/tmp/oit_remote_install.cfgto
echo 'ALLOWPOPUP=allow' >/tmp/oit_remote_install.cfgwhere allow indicates, allow pop-up. Pop-up displays for all users. Screen Recording permission is granted in Security & Privacy configuration.
or
-
'ALLOWPOPUP=never' >/tmp/oit_remote_install.cfgwhere never indicates, never display pop-up. There is no screen recording.
or
'ALLOWPOPUP=<user>' >/tmp/oit_remote_install.cfgwhere <user> is the username of the user for whom you want the pop-up to display. Pop-up displays for the specified user only. This user grants Screen Recording permission in Security & Privacy configuration for the computer.
-
-
Modify the optional parameters, such as the password, by entering the parameter after "=" and removing "#" to uncomment the line.
For example, change
#echo 'PASSWORD=' >> /tmp/oit_remote_install.cfgto
echo 'PASSWORD=<your_password>' >> /tmp/oit_remote_install.cfg -
Save your changes. Close and double-click to run.
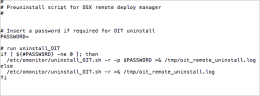
preuninstall script
This script contains the parameters for uninstalling the Mac Agent.
The following is an example of the preuninstall script.
preuninstall script parameters
-
Password: Only if required
Modifying the preuninstall script
-
Copy the
preuninstallscript to your desktop or another folder that is easily accessible. -
Modify the password parameter by entering a password if one is required.
-
PASSWORD=to
PASSWORD=<your_ password> -
Save your changes. Close and double-click to run.
IT Viewer Configuration Profile File
The configuration profile is used with the silent installation solution for mass deployment. Silent installation is supported from macOS Mojave 10.14. (See Mac Agent Mass Deployment using JAMF.)
IT View Configuration Profile Files:
-
IT Viewer macOS 10.x.mobileconfig (not signed, obfuscated)
-
IT Viewer macOS 10.x.signed.mobileconfig (signed, not obfuscated and read-only)
Optionally, you can modify the configuration profile and change the process name from it's default, "logger".
Modifying the IT Viewer Configuration Profile File
Modify the configuration profile for obfuscation.
-
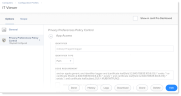
From the JAMF Web Console Dashboard, click the Computer button and select Configuration Profiles from the menu on the left-side. The Configuration Profiles screen displays.
-
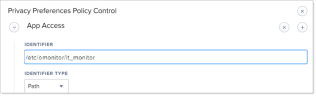
Select the IT Viewer Configuration policy and then select Privacy Preferences Policy Control option.
The Privacy Preferences Control screen displays.
-
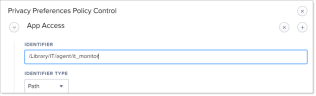
Click Edit and in App Access area, in the Identifier field, replace "logger" with the name you want. (In the example, "logger" is replaced with "it_monitor".)
-
Scroll down to the next App Access area, and in the iIdentifier field, replace "logger" with the name you want.
-
Save your changes.
postinstall script
This script is used when deploying Mac Agents in an mTLS client environment.
This script is relevant from version 7.10.x.
Before you run this script, see Securing Mac Agent Certificate for mTLS and Preparing the Client (Agent) Certificate for Mac in an mTLS Environment.
The following are examples of the parameters in the postinstall script:
- INSTALL_DIR: location where the .pem <
CLIENT-i01-c01.pem> and .pfx <CLIENT-i01-c01.pfx> files will be created when deployed (for example, <$WORKDIR/install>. - CLIENTCERT_PFX_FILE: Name of the client certificate .pfx file. In the example,
CLIENT-i01-c01.pfx. - CLIENTCERT_PEM_FILE: Name of the client certificate .pem file. In the example,
CLIENT-i01-c01.pem. - PEM_PASS: Password for .pem file
For more information, see Preparing the Client (Agent) Certificate for Mac in an mTLS Environment.
For more information about enabling the Mac Securing Mac Agent Certificate for mTLS.
postinstall Script Example
#!/bin/bash
#
# Copyright 2020 ObserveIT Ltd. All rights reserved.
# Use is subject to license terms.
#
# Postinstall script for OSX MTLS client certificate deployment
#
LOG_FILE=/tmp/it_mtls.install.log
#INSTALL_DIR=<Value of '--install-location' parameter when running the 'pkgbuild' command>
#CLIENTCERT_PFX_FILE=<$INSTALL_DIR/<Client certificate pfx file name>
#CLIENTCERT_PEM_FILE=<$INSTALL_DIR/<Client certificate pem file name>
#PEM_PASS=<pem file password>
cleanup()
{
echo "Cleaning up..." >> $LOG_FILE
rm -f $CLIENTCERT_PFX_FILE $CLIENTCERT_PEM_FILE
}
echo "Running $0 - start postinstall client certificate deployment script" > $LOG_FILE
if [ ! -r $CLIENTCERT_PFX_FILE ]; then
echo "Error: File $CLIENTCERT_PFX_FILE not found or unreadable" >> $LOG_FILE
cleanup
exit 1
fi
if [ ! -r $CLIENTCERT_PEM_FILE ]; then
echo "Error: File $CLIENTCERT_PEM_FILE not found or unreadable" >> $LOG_FILE
cleanup
exit 1
fi
echo "About to execute: security add-trusted-cert -d -r trustAsRoot -k /Library/Keychains/System.keychain $CLIENTCERT_PEM_FILE" >> $LOG_FILE 2>&1
security add-trusted-cert -d -r trustAsRoot -k /Library/Keychains/System.keychain $CLIENTCERT_PEM_FILE >> $LOG_FILE 2>&1
if [ $? != 0 ]; then
echo "Error: Failed to trust certificate $CLIENTCERT_PEM_FILE" >> $LOG_FILE
cleanup
exit 1
fi
loggerBinary=logger ### Replace with obfuscated name if required
echo "About to execute: security import $CLIENTCERT_PFX_FILE -k /Library/Keychains/System.keychain -T \"/etc/omonitor/$loggerBinary\" -T \"/etc/omonitor/service\" -T \"/etc/omonitor/oitcons\" -T \"/etc/omonitor/itAppWrapper\" -T \"/etc/omonitor/WarningNotification.app\" -T \"/etc/omonitor/BlockingMessage.app\" -P ****" >> $LOG_FILE 2>&1
security import $CLIENTCERT_PFX_FILE -k /Library/Keychains/System.keychain -T "/etc/omonitor/$loggerBinary" -T "/etc/omonitor/service" -T "/etc/omonitor/oitcons" -T "/etc/omonitor/itAppWrapper" -T "/etc/omonitor/WarningNotification.app" -T "/etc/omonitor/BlockingMessage.app" -P $PEM_PASS >> $LOG_FILE 2>&1
if [ $? != 0 ]; then
echo "Error: Failed to import certificate $CLIENTCERT_PFX_FILE" >> $LOG_FILE
cleanup
exit 1
fi
echo "Successfully installed client certificate" >> $LOG_FILE
cleanup
exit 0
Create pkg destination directory, e.g. $WORKDIR/install
Create the .pkg by running the following command:
/usr/bin/pkgbuild --identifier com.it.pkg.cert --version 1.0.0.0 --root $WORKDIR/certs --scripts $WORKDIR/scripts --install-location $WORKDIR/install $WORKDIR/install/mtls_cert.pkg